Protect Yourself from Ransomware
by Larry Kollar
(Reprinted from my personal blog. Original post date: May 10, 2016. Updated.)
You’re working away one evening, when your computer locks up and shows you something like this:
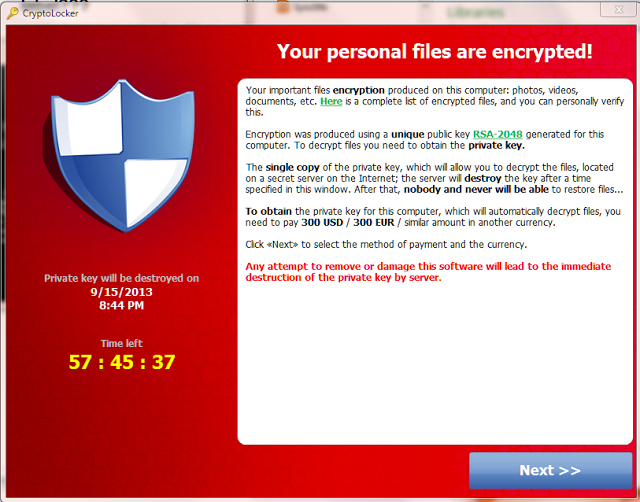
Unfortunately, it’s not the plot of a bad cyberpunk novel. It recently happened to an acquaintance. Last year, I wrote about Three Ways to Crash-Proof Your Writing, and the tips are still useful. But you might need a little more caution when it comes to ransomware.
What’s Happening In There?
In short, a PC infested with ransomware establishes a connection with its operator. The PC might run normally for a while after getting infested, but at some point the ransomware begins encrypting data files with common extensions like .doc, .psd, .jpg, .zip, and so forth. When it’s done, it displays a ransom note like the one shown above. Operators usually demand Bitcoin payments, because they can’t be traced. Some ransomware allows you to decrypt a single file, thus proving they have the key, and usually give you a few days to get the Bitcoin you need to pay up. If you wait too long, the ransom goes up or the operator destroys the key (which means you’re permanently hosed). Scary crap.
Unfortunately, Dropbox is not a failsafe. Ransomware encrypts everything on your hard drive, and if you have Dropbox mirrored, it nails your files there as well.
George R. R. Martin famously does his writing on an air-gapped (i.e. no network connection) PC, running WordStar on MS-DOG [sic]. While he uses WordStar for its simplicity, he also has little to fear from most stripes of malware. Such a setup works well in the traditional publishing realm, where they still prefer to start from paper drafts, but it’s not a bad idea for indies. One might balk at the expense of a second computer—but the typical ransom these days is $500, and you can get a netbook for half that. It’s not bad insurance. Remember, if you’re trying to make money at writing, this is a business. Ransomware is one more disaster to plan for.
Let’s assume that, because you have no room or money for an air-gapped computer, or need to have a browser handy for research, that’s out of the question. What else can you do? Read on…
GROW
Right now (July 2017), the most effective way to avoid ransomware is to GROW (Get Rid Of Windows). Move to MacOS, Linux, or OpenBSD if you possibly can. This is likely a temporary advantage, but it may be a couple of years before ransomware goes beyond Windows. And if the techie press breathlessly reports every minor instance of MacOS malware found in the wild, they’ll be so beside themselves over MacOS ransomware that we’ll never hear the end of it. In other words, it won’t sneak up on us. Actually, I expect iOS malware first, because iDevices are so popular.
As a possible workaround, install a virtualization tool such as VirtualBox, VMware, or Parallels and run a separate operating system inside the virtualizer for Internet access. This isn’t foolproof—ransomware can encrypt virtual drives at a stroke, if you make a mistake—but it’s a little safer.
Stay Up to Date
That should go without saying, but it’s so easy to skip those updates in the middle of a project. Sometimes, there’s good reason for that; updates have been known to hose a working PC. If you’re doing your backups, though, you should be able to revert when needed. Don’t forget to check the backups, on occasion, to make sure important data is still good.
Don’t let your virus/malware protection slide, either. Keep them updated.
Avoid Common Attack Vectors
Currently, there are several common, well-known ways malware (including ransomware) can infest your system:
- Dodgy attachments in spam
- Compromised ad servers
- Websites with infectious Javascript or Flash
Thus, installing ad-blockers and Flash blockers in your browser(s) can offer protection from so-called “drive-by” attacks. Turning off Javascript, once a common trick to speed up browsing and stop useless visual effects, is making a comeback as well. Try it with your favorite websites and see if you can live without it. You can certainly live without it trying to download garbage onto your computer.
Spammers will never go away, even if there’s a special place in Hell for them. They are paying more attention to grammar these days, so you can’t always catch them out by stilted language anymore. Some spam is really phishing, attempting to get you to click a link or open an attachment that Does Not End Well For You. If you’re not expecting that payroll statement from someone you’ve never heard of, don’t open it. If your bank sends you a report about fraudulent activity about your account… it’s not really your bank. A real bank fraud department will call you, verify your identity, then go over a few transactions. (I’ve been there.) In short, don’t open attachments you aren’t expecting.
Pull a Dirty Trick
Since ransomware only encrypts files with known extensions, consider renaming crucial backup files. Instead of GreatAmericanNovel.zip, rename it with a random extension like GreatAmericanNovel.e7b. If you have a thousand photos you don’t want to lose, copy them somewhere else now. Anything your computer can’t access directly, as if it’s on your hard drive, is safe. To be honest, I’m not sure how Google Drive works with saving local copies on a computer; I do know you have to start the Drive app to get the latest onto a tablet or phone, though.
In short, the goal is keeping your computer clean. Failing that, you want to recover with as little hassle as possible. Anticipate the disaster, have a plan, and execute.
References
If you want to dig a little deeper, here’s a couple of links that might be useful:
- Sophos: The Current State of Ransomware
- HEAT Software: How Do You Protect Your System from Ransomware?
Your Turn
Have you been clobbered by ransomware? Do you have some prevention or recovery tips? The comment section is open.
Subscribe via RSS
